Tag: Staff Onboard Reading
-

Employe Benefit Equipment of Portable Power Station User Guideline
CAUTION Please read carefully and understand every single words inside the paragraph before you use the portable power station. Disclaimer DDM Group shall not be held responsible or liable for any loss, theft, explosion, or damage caused by the portable power station, nor for any third-party liabilities arising from such incidents. Furthermore, DDM Group will…
-
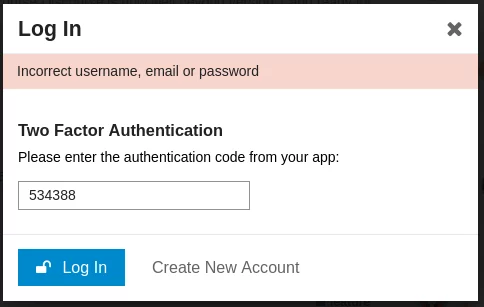
How to Enable 2FA in Facebook Personal Account
Facebook Personal Page Facebook Personal Page is one of the products under the umbrella of Meta, inc product fleet. While you can easily access your Facebook Personal Page by logging in via www.facebook.com, there are many interface from different products under Meta, inc. will drive you to the interface of Facebook Personal Page, including but…
-
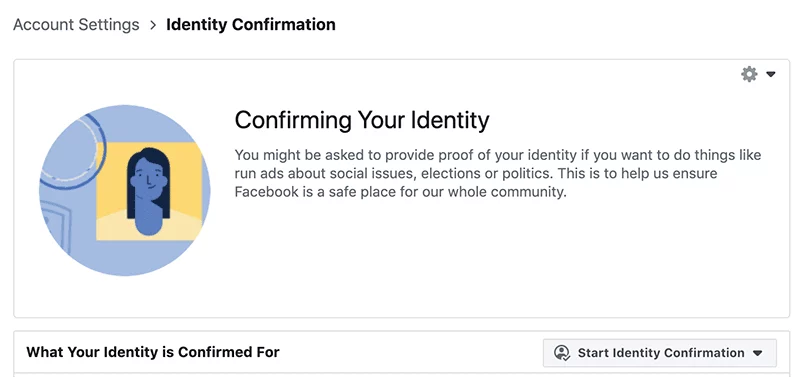
Confirm Identity for your Facebook Personal Page
Definition Facebook Personal Page Facebook Personal Page is one of the products under the umbrella of Meta, inc product fleet. While you can easily access your Facebook Personal Page by logging in via www.facebook.com, there are many interface from different products under Meta, inc. will drive you to the interface of Facebook Personal Page, including…
-

Employee Benefit in DDM Group
Introduction The principal of decising the degree of Employee Benefit (v20250928) provided to the employee in DDM Group is based on the contribution that the employee had been delivered to the Company. Employee Benefits Education Amazon Kindle Book Store A/c Amazon Kindle Book Store account is an Amazon A/c owned by DDM Group which can…
-

Anti-Virus Software Installation
Introduction The objective of installing anti-virus software on employee laptops is to ensure the security and integrity of company data and systems. By providing comprehensive protection against malware, viruses, and other malicious threats, anti-virus software helps prevent data breaches, system disruptions, and unauthorized access. Avast Anti-Virus Avast Anti-Virus is a comprehensive security solution designed to…
-

Non-Disclosure Agreement for Employee in DDM Group
This Non-Disclosure Agreement (the “Agreement”) , version v20250108, is made and entered into as of the Submission Date of the Form, by and between Diamond Digital Marketing Group (“Disclosing Party”), and the Employee (“Receiving Party”). 1. Definition of Confidential Information For purposes of this Agreement, “Confidential Information” includes all information or material that has or…
-

Linking Personal Linkedin Profile to Business Linkedin Page
-

Employees Code of Conduct in DDM Group
Introduction At DDM Group, we are committed to maintaining the highest standards of integrity, professionalism, and ethical behavior in all of our business activities. Our Code of Conduct serves as a guide for all employees, outlining the principles and values that underpin our corporate culture and decision-making processes. By adhering to these guidelines, we ensure…
-

VPN Installation
Definition VPN A VPN (Virtual Private Network) is a technology that creates a secure and encrypted connection over a less secure network, such as the internet. VPNs are commonly used to protect privacy, ensure online security, and access restricted content. Imagine two fortified castles, each representing a VPS, located in different kingdoms. These castles are…
-
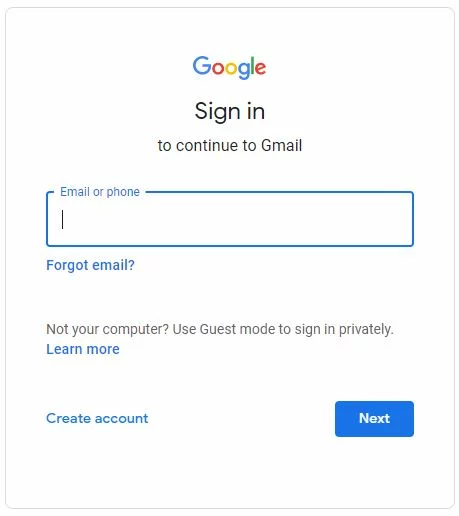
Login Domain Email via Gmail Interface
