Category: Knowledge Base
-

How to Assign Remote Desktop Access Rights to Technical Support
Definition What Problems Remote Desktop Access Solves Step By Step – As a Assignor Prerequisite Step By Step Step By Step – As a Assignee Prerequisite Setup Process for the Assignor (Granting Access) Step 1: Install Chrome Remote Desktop Step 2: Enable Remote Access Step 3: Share Access with the Assignee Step By Step –…
-
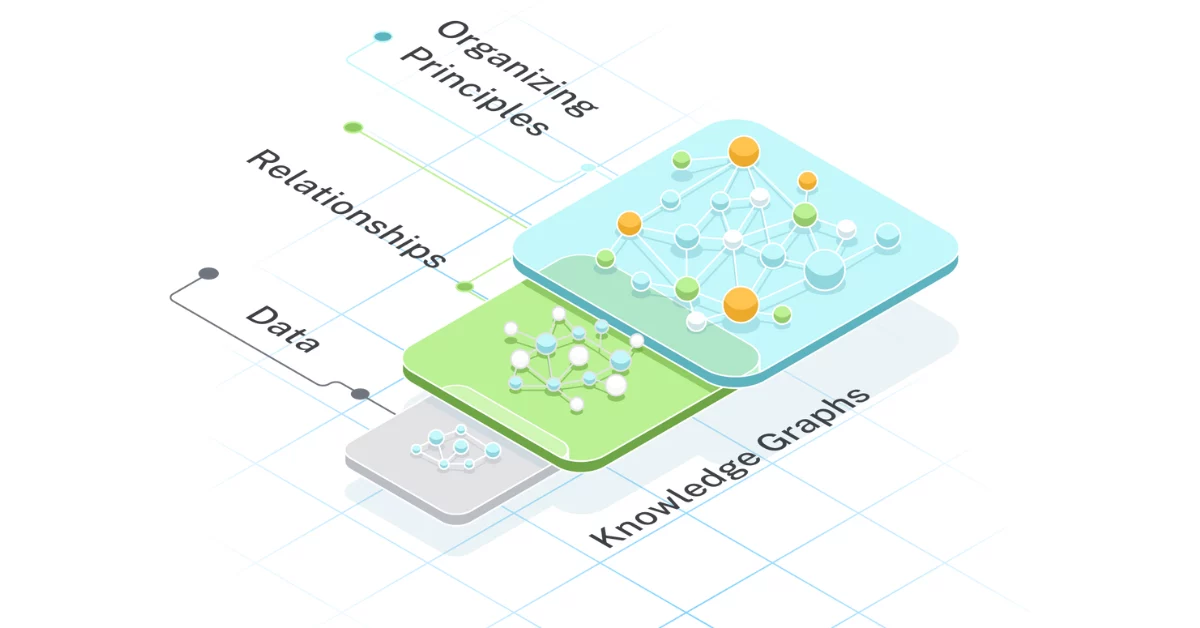
Data Schema of Relational Table Importing to Graph Database – Execution
Introduction In the earlier article titled Data Schema of Relational Table Importing to Graph Database – Dimensionality, we explored how to observe real-world data and transform it into a digitised format within a Relational Database. The greater the dimensions we account for, the higher the fidelity with which the Relational Database represents reality. In this…
-
Data Schema of Relational Table Importing to Graph Database – Dimensionality
Definition Relational Table The Table is the fundamental components inside a Relational Database which stores data in tabular format using Column and Row to coordinate a specific Value (i.e. the Cell). Form and Table (i.e. Tabular format) are everywhere in your daily life. Data Schema in Relational Database A data schema in a Relational Database…
-
What Problem Patterns bGraph Is Going to Solve
Introduction bGraph is an SaaS developed in-house by Diamond Digital Marketing Group which can be categorised as a GraphRAG web application serving as an Enterprise Knowledge Graph. To better understand what GraphRAG exactly is, it is imperative for us to start with a real world problem pattern Real World Problem Patterns The definition of profit…
-

Assign Youtube Studio Access Rigths to Others
Definition Google Ads Google Ads is an online advertising platform developed by Google, where advertisers can create ads to promote their products, services, or content. These ads can appear across Google’s vast network, including the Google Search results, YouTube, Gmail, and various websites within the Google Display Network. Google Ads , Google Marketing Platform and…
-

Assign Google Tag Manager Access Rigths to Others
Definition Google Tag Manager Google Tag Manager (GTM) is a free tag management system that allows you to manage and deploy marketing tags (small snippets of code) on your website or mobile app without modifying the underlying code. It simplifies the process of adding and updating tags, such as those for Google Analytics, Google Ads,…
-

Assign Google Ads Access Rigths to Others
Definition Google Ads Google Ads is an online advertising platform developed by Google, where advertisers can create ads to promote their products, services, or content. These ads can appear across Google’s vast network, including the Google Search results, YouTube, Gmail, and various websites within the Google Display Network. Google Ads , Google Marketing Platform and…
-

Assign Shopify User Access Rights
-
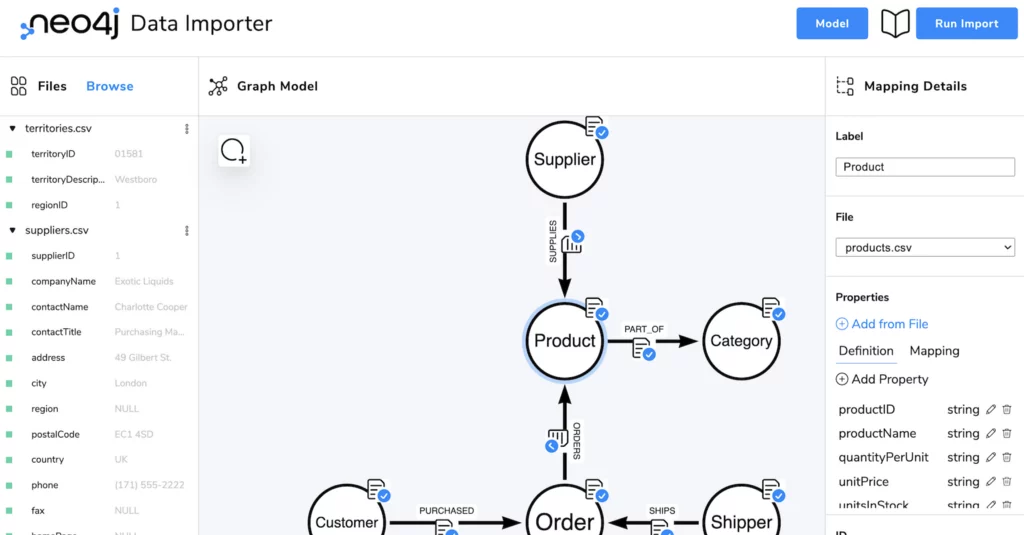
bGraph Architecture – Model Data
Introduction The objective of this article is to provide a blueprint which demonstrates and enumerates all the technical stacks used to build the bGraph. Although using a Graph Database is a perfect tool to illustrate this kind of blueprint, ironically, we cannot use the Graph Database to demonstrate how to build a Graph Database because…
-

Assign Google Search Console Access Rights to Others
Definition Google Search Console (GSC) Google Search Console is a free web service offered by Google that helps website owners, webmasters, and SEO professionals monitor and maintain their site’s presence in Google search results. It’s like a communication portal to connect among Webmaster, Google Search Engine and the Target Website. Access Rights Access rights refer…
